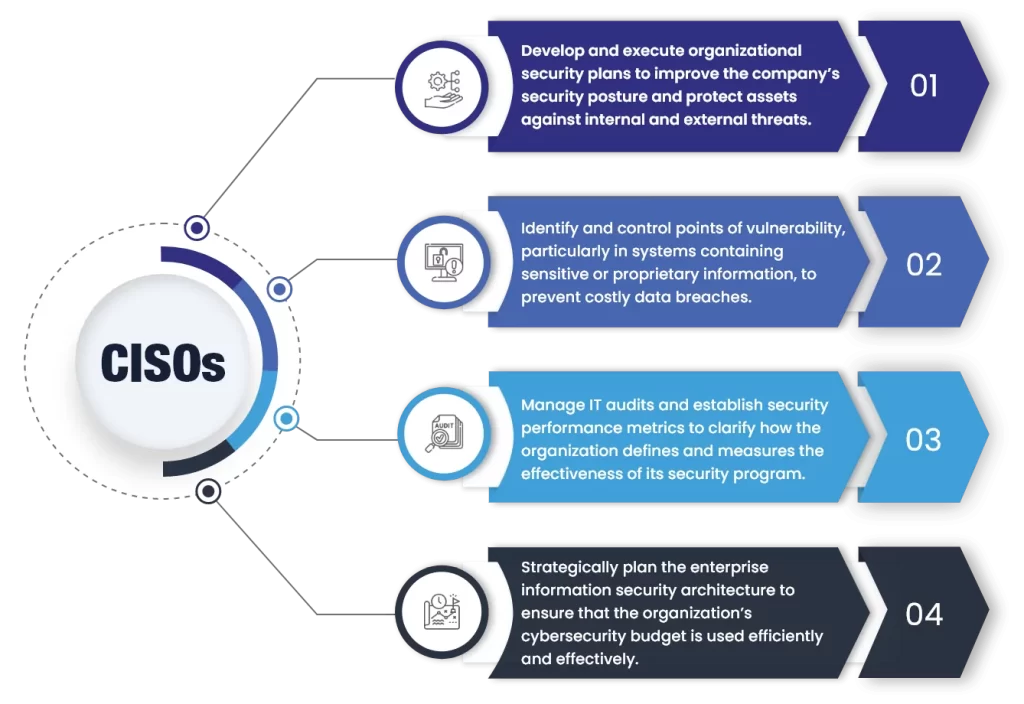
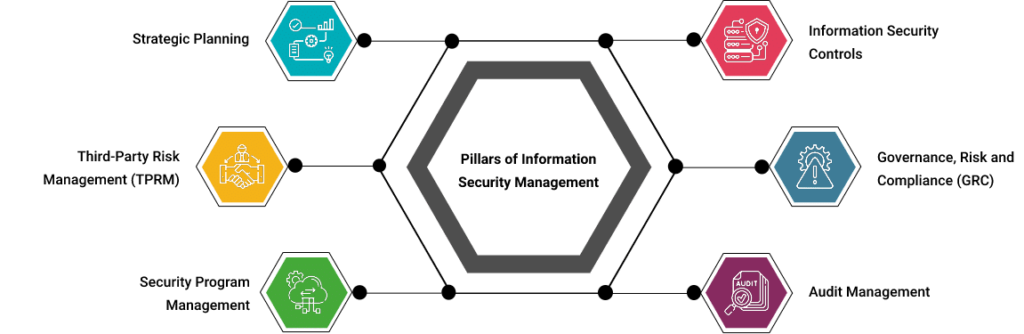
Understanding the Role of a Security Operations Center
What Are the Responsibilities of a Security Operations Center Team? A security operations center (SOC) is essential for any organization in today’s data-driven world. A SOC is a group of cybersecurity experts responsible for monitoring and protecting an organization’s networks and information. SOC teams play a critical role in keeping organizations secure. This article will…
The post Understanding the Role of a Security Operations Center appeared first on Cybersecurity Exchange.