Basic Networking Part 2 — What Is Data Packets?
Introduction
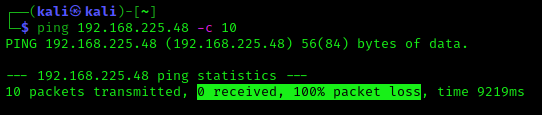
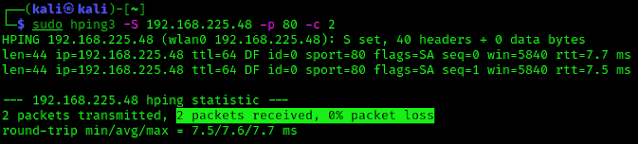
It turns out that packets are involved in everything you do on the Internet. Packet is a basic unit of communication over Computer Network. Every Web page you receive, every e-mail you write is also made up of packets. Packet switched networks are networks that transport data in small packets.
What is a Packet?
On the Internet, an e-mail message is broken down into bytes of a specified size. These are the individual packages. Each packet contains information that will assist it in reaching its destination, such as the sender’s IP address, the intended receiver’s IP address, and a number that tells the network how many packets this e-mail message has been broken into. The data is carried in packets by the Internet’s protocols, Transmission Control Protocol/Internet Protocol (TCP/IP). Each packet contains a portion of your message’s body. Typically, a packet has 1,000 to 1,500 bytes.
Each packet is subsequently sent to its destination through the best available route, which may or may not be shared by all other packets in the message. This improves the network’s efficiency. First, the network can millisecond-by-millisecond balance the load across several pieces of equipment. Second, if a piece of network equipment fails while a message is being sent, packets can be routed around the fault, ensuring that the complete message is delivered.
Data Packet Structure
Most network packets are split into three parts:
Header – The header contains information about the data that the packet will carry. These instructions may contain the following:
- The length of the packet (some networks have fixed-length packets, while others rely on the header to contain this information).
- Synchronization (a few bits that help the packet match up to the network).
- Packet number (which packet this is in a sequence of packets).
- Protocol (on networks that carry multiple types of information, the protocol defines what type of packet is being transmitted: e-mail, Web page, streaming video etc.)
- Destination address (where the packet is going).
- Originating address (where the packet came from).
- Other technical data.
Payload – Also known as a packet’s body or data. This is the data that the packet is sending to its intended destination. If the payload of a packet is fixed-length, it may be padded with blank data to make it the proper size.
Trailer – The trailer, also known as the footer, usually contains a handful of bits that inform the receiving device that the packet has ended. It may also include some form of error detection. Cyclic Redundancy Check is the most prevalent type of error checking employed in packets (CRC).
CRC is a really cool program. In some computer networks, this is how it works: It puts together the sum of all the 1s in the payload. The result is saved in the trailer as a hexadecimal value. The receiving device adds up the 1s in the payload and compares the result to the trailer’s value. The packet is valid if the values match. However, if the values do not match, the receiving party will be notified.
Conclusion
Consider how an e-mail message might be divided into packets as an example. Assume you’re sending an e-mail to a friend. The size of the e-mail is approximately 3,500 bits (3.5 kilobits). You’re sending it across a network that employs 1,024-bit fixed-length packets (1 kilobit). Each packet contains a 96-bit header and a 32-bit trailer, leaving 896 bits for the content. Four packets are required to separate the 3,500 bits of message into packets (divide 3,500 by 896). The payload will be 896 bits in three packets and 812 bits in the fourth. The contents of one of the four packages would be as follows:
The proper protocols, as well as the originating address, will be included in the header of each packet.