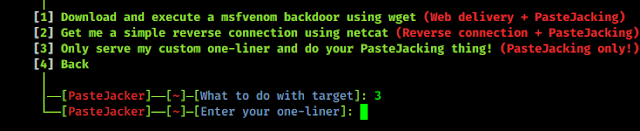
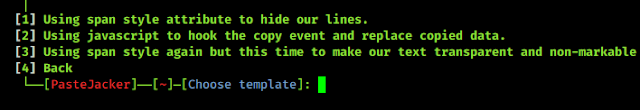
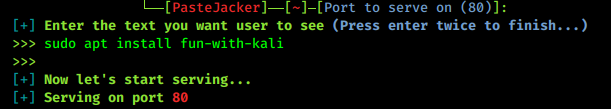
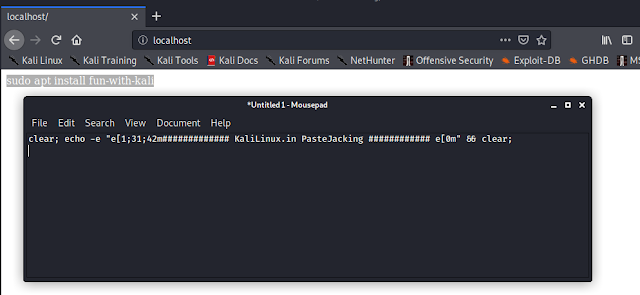
Basic Networking Part 4 — What is Port?
Introduction
In our many previous articles we had referred the word “port“. In our this Basic Networking Series, we are going to cover about port. Here without being much technical, we just learn the basics of port with a cybersecurity point of view. This will be understanding port for absolute beginners.
What is Port?
The theory behind port is hard to explain for beginners (excuse us), but we will try our best. In a computer network port is a end point of communication. For an example, we had installed IP camera on our driveway, which is connected on our network. Now it can be accessed from our computer, here IP address and network ports used. Our router is dependent on ports to route data and we can access our camera from our computer. To understand this better let’s jump on little bit technical shit.
In computer networking, a port is a virtual end point of communication. A port is a 16 bit number, i.e. it can go from 1 to 65535. A modern day device can do a lot of things at a particular time. For each type of service there will be a different port, for the same destination IP.
Mainly, there are two protocols in the networking that uses port numbers, they are, Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP:- TCP handles transmissions. It sends information from one computer to another by a direct connection. Both computers stays connected during this process.
UDP:- With the help of UDP, the computer hardware are can create data packets and send them on the network. It didn’t make connection during transfer.
TCP is slower than UDP, but TCP can retransmit the lost data due to the connection between the devices.
What is Port Numbers ?
Well, as we discussed earlier, port number is a logical address assigned for each process that uses networking for communication.
Network based on TCP and UDP mostly use port numbers up to 65535. The application it self can change it’s port number, but generally it uses common global port numbers, like port number 80 is for HTTP, port 23 for telnet, port 25 for email, port number 3389 generally used for remote desktop protocol. There is a list for all port number and their uses.
What is Port Forwarding ?
When a remote system/computer wants to make a connection with our computer then we need to allow this by opening required port of that service, so the data packets can enter on our system. Remember that port is the end point! This is the very basic concept of port forwarding. We can manage our port forwarding from our router’s settings. Various routers have various type of settings so we need to check our router. We can easily learn how to forward our port by searching internet “How to port forward on router name“. We have discussed about SSH port forwarding, but that is different thing which uses SSH tunneling.
Summary
Cybersecurity learners must have a clear idea on port forwarding. Remote desktop, ssh, exploiting machines etc usually requires port forwarding. IP addresses and ports are very useful things of networking. These are the most basic things of ports.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.