December 3, 2024
What is a Security Operations Center (SOC)?
A Security Operations Center (SOC) is an exclusive security facility within an organization responsible for monitoring and responding to security incidents in a 24×7 format. The primary goal of a SOC is to detect, analyze, and respond to threats and security incidents using a combination of security tools, techniques, and policies. This blog explains a SOC’s functions, structure, types, and importance.
Functions of a SOC
A SOC has several vital functions that are essential for maintaining an organization’s security posture. These include:
- Continuous Monitoring: The SOC constantly monitors an organization’s IT infrastructure to look for any signs of security breaches. It involves using advanced monitoring tools and technologies to collect and analyze data from various sources, such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
- Incident Detection and Response: If a potential threat is detected, the SOC is responsible for investigating the incident to determine its severity and business impact. The SOC team then takes appropriate measures to mitigate the threat, including isolating affected systems, applying patches, or engaging in more in-depth remediation tactics.
- Threat Intelligence: SOC analysts leverage threat intelligence to stay ahead of any potential threats. This involves gathering and analyzing information about emerging threats and vulnerabilities from various external sources, such as cybersecurity news feeds, threat intelligence platforms, and information sharing and analysis centers (ISACs).
- Incident Management: Effective incident management is critical to a SOC’s function. This includes developing and following incident response plans, conducting post-incident analysis to learn from security events, and continuously improving security protocols and processes.
- Compliance and Reporting: The SOC also bears the burden of ensuring that organizations comply with relevant data protection regulatory requirements and maintain industry standards. This involves generating detailed reports on security incidents and the measures taken to address them, which are critical for audits and regulatory compliance.
Structure of a SOC
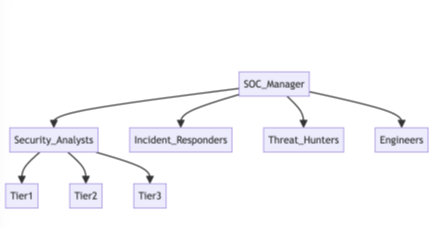
A SOC is typically structured with a team of skilled professionals and advanced technology platforms. The critical roles within a SOC include:
- Security Analysts: They are the frontline defenders who monitor systems, analyze alerts, and investigate incidents. They are often categorized into levels (Tier 1, 2, and 3) based on their experience and expertise.
- Incident Responders: These are specialists who take the lead when an actual incident occurs. They coordinate efforts to contain and eradicate threats, recover systems, and ensure everyday operations are resumed as quickly as possible.
- SOC Manager: The SOC manager manages the entire operation, ensuring that all processes are correctly followed, resources are adequately allocated, and the SOC meets its strategic objectives.
- Threat Hunters: These professionals search for threats that automated tools may not have detected. They adopt advanced techniques and threat intelligence to identify and mitigate potential risks before they take shape.
- SOC Engineers: SOC engineers are responsible for maintaining and optimizing the technical infrastructure/resources of the SOC. This includes configuring and managing security tools, updating them, and integrating/implementing new technologies as needed (Bykowski, 2023).
Types of SOCs
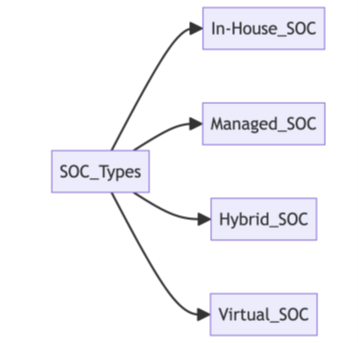
Organizations can choose from different types of SOCs depending on their size, budget, and security requirements. The main types of SOCs include:
- In-House SOC: Managed and operated by the organization, this type provides complete control over the security operations. An in-house SOC is very demanding from the perspective of resources and skilled professionals. Hence, it is feasible only for large organizations or those responsible for monitoring critical larger networks.
- Managed SOC: This type is outsourced to a Managed Security Service Provider (MSSP), which handles all the SOC operations. This option is cost-effective for organizations that would require more resources to build an in-house SOC.
- Hybrid SOC: This type combines elements of both in-house and managed SOCs. The organization retains some control over its security operations while leveraging external expertise and resources for specific functions.
- Virtual SOC: This is a decentralized SOC wherein analysts and tools are not located in a single physical location. This model leverages cloud-based tools and remote teams to provide flexibility and scalability (Houghton, 2021).
Technology and Tools in a SOC
A SOC relies on various tools and technologies to perform its functions effectively (Manage Engine, n.d.). Some of the essential tools include:
- Security Information and Event Management (SIEM): The SIEM system collects and correlates data from various sources to provide real-time analysis of security alerts. It is a cornerstone technology for any SOC, which assists with detecting and managing security incidents.
- Intrusion Detection and Prevention Systems (IDS/IPS): These solutions are used for monitoring network traffic for suspicious activity but differ slightly in their key roles. Where IDS detects and issues alerts for probable network intrusions, IPS actively prevents malicious activity by blocking or dropping packets.
- Endpoint Detection and Response (EDR): EDR solutions focus on monitoring and securing endpoints (e.g., computers and mobile devices) to detect and respond to malicious activities.
- Threat Intelligence Platforms (TIP): TIPs aggregate data from multiple threat intelligence sources to provide actionable insights and help SOC analysts stay informed about the latest threats.
- Security Orchestration, Automation, and Response (SOAR): SOAR platforms enable the automation of security operations, helping SOC teams respond to incidents in a more efficient and effective manner.
The Importance of a SOC
A SOC is essential for any organization to protect its digital assets and maintain a strong security posture. Here are a few reasons why a SOC is indispensable:
- 24/7 Monitoring: Cyber threats can occur anytime, making round-the-clock monitoring crucial. A SOC ensures that someone is always monitoring the organization’s IT environment and is ready to respond to threats as they arise.
- Pre-emptive Threat Management: By leveraging threat intelligence and pre-emptive threat hunting, a SOC can identify and mitigate risks beforehand to avoid significant damage.
- Rapid Incident Response: A SOC is designed to respond to security incidents swiftly and effectively, minimizing the potential impact on the organization.
- Regulatory Compliance: As data protection and integrity are primary concerns among digital users across the globe, stringent regulations have been levied across industries. A SOC ensures that the organization meets these requirements, thereby avoiding potential fines and legal repercussions.
- Enhanced Security Posture: Continuous monitoring, incident response, and threat intelligence activities conducted by a SOC contribute to a robust security posture, making it harder for attackers to succeed.
Challenges in Operating a SOC
Operating a SOC is not without its challenges. Some of the common difficulties faced by SOCs include:
- Alert Fatigue: The volume of alerts and false positives generated by security tools can overwhelm SOC analysts, leading to potential oversights and skewed results. Implementing effective alert management and prioritization strategies is essential.
- Skill Shortage: The cybersecurity industry faces a talent shortage, making it challenging to find and retain skilled SOC personnel. Continuous training and development programs are crucial to address this issue.
- Keeping Up with Evolving Threats: With cyber threats constantly evolving, SOCs must stay up-to-date with the latest attack vectors and techniques. This requires ongoing investment in training, tools, and threat intelligence.
- Integration of Tools: SOCs often use various vendor tools, which can lead to integration challenges. Ensuring seamless interoperability between tools is critical for efficient SOC operations.
- Budget Constraints: Maintaining a SOC can be expensive, and organizations may face budgetary constraints. This limits their ability to invest in necessary resources and technologies.
Building an Effective SOC
To build an effective SOC, organizations should focus on the following key areas:
- Defining Clear Objectives: Establishing clear objectives and key performance indicators (KPIs) for the SOC helps measure performance and ensure alignment with the organization’s overall security strategy.
- Invest in the Right Tools: Selecting and deploying the appropriate tools and technologies that fit the organization’s needs, including SIEM, EDR, TIP, and SOAR platforms.
- Hire and Train Skilled Personnel: Recruit skilled professionals and provide them with continuous training to ensure they are aware of the latest cybersecurity trends and technologies.
- Develop Robust Processes: Establishing and documenting robust incident detection, response, and management processes in addition to periodic review and upgrade of involved policies and protocols.
- Leverage Threat Intelligence: Utilizing threat intelligence to enhance the SOC’s ability to detect and respond to emerging threats.
- Foster Collaboration: Promoting collaboration within the SOC team as well as with other departments, such as IT and threat management, to implement a holistic security approach.
- Conduct Regular Assessments: Regularly assess the SOC’s performance through audits and testing, using the results to identify gaps and implement the necessary changes for patching and threat mitigation.
Conclusion
A Security Operations Center is critical to an organization’s cybersecurity strategy. By providing continuous monitoring, proactive threat management, and rapid incident response, a SOC helps protect an organization’s digital assets and ensures compliance with regulatory requirements. Although building and maintaining an effective SOC requires investment in the right tools, skilled personnel, and robust processes, the benefits far outweigh the challenges. Establishing a well-functioning SOC is vital for organizations looking to strengthen their cybersecurity posture.
Reference
Bykowski, K. (2023, January 12). The Key SOC Team Roles and Responsibilities. Swimlane. https://swimlane.com/blog/soc-team-roles-responsibilities/
Houghton, M. (2021, August 16). The Different Types of Security Operation Centre (SOC). Aztech IT. https://www.aztechit.co.uk/blog/types-of-security-operation-centre-soc
Manage Engine. (n.d.). What are the tools and technologies used in SOCs? https://www.manageengine.com/log-management/siem/soc-tools-technologies.html
Tags
About the Author
The post Security Operations Center: The Nervous System of Cyber Defense appeared first on Cybersecurity Exchange.
Article posted by: https://www.eccouncil.org/cybersecurity-exchange/security-operation-center/soc-system-for-cyber-defense/
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.
