January 27, 2024
Becoming anonymous is a very good way to hide ourself form all kind of surveillance. But we get only few option because VPN is really bad, specially those free one. Free VPN’s keeps logs and we can be traced.
We can use TOR network, not the browser only. Tor can’t be traced easily it is very hard (practically close to impossible). Read our detailed article on
This is not the first, previously we made an article on AnonSurf, but that tool is not updated in last 3 years and we got a lot of issues.
In today’s article we gonna talking about Nipe. This perl script enables us to directly route all our traffic from our computer to the Tor network through which we can use the internet anonymously without having to worry about tracked or traced back.
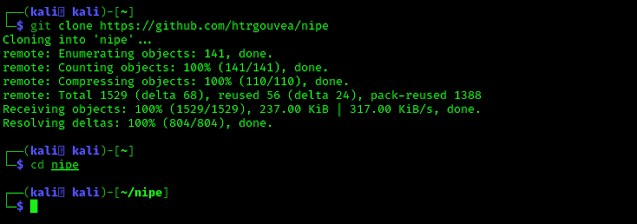
First of all we need to clone this repository from GitHub by using following command:
Then it will copied to our system we can go inside the directory using cd command:
The screenshot of the above commands is following:
Now we need to install libraries and dependencies by using following command:
Now for new comers cpan might be a strange command, cpan helps to install packages or modules for Perl. In simple words we can say ‘Python have pip‘ & ‘Perl have cpan‘.
After this we can install this Perl script using following command:
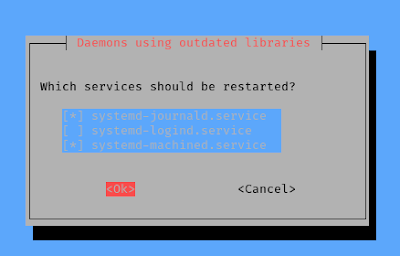
Then the installation process will start. After the installation we got a notification that some services need to restart, here we press “TAB” button and select OK by pressing ENTER, as we can see in the following screenshot:
After this we can say that our installation process is done. Now we are ready to ROCK.
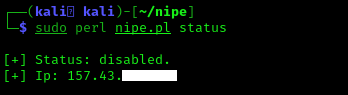
First of all we check the status of NIPE tool by applying following command:
The screenshot of the command is following:
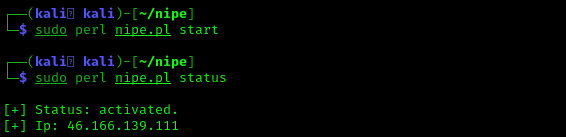
In the above screenshot we can see that NIPE is disabled here but we can start it using following command:
After applying these command NIPE services will be started, now again if we can check the status by applying sudo perl nipe.pl status command then, we can see the output as the following screenshot:
Now we need to test our IP by opening dnsleaktest website to make sure that our original IP address is hided. Checking this will be a good test for NIPE tool beneficial for everyone.
When we are done we can off this Tor gateway and get back to our original IP address by applying following command:
After applying the above command NIPE will stop and we get back our original IP. We can check the status, as we did in the following screenshot:
NIPE makes Tor network our default gateway. This is how we can anonymise our total Kali Linux system. This process is enough secure. Practically cracking Tor is close to impossible but as we know theoretically everything is possible.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxInfamily, join our Whatsapp Channel & Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.