A CEH’s Perspective
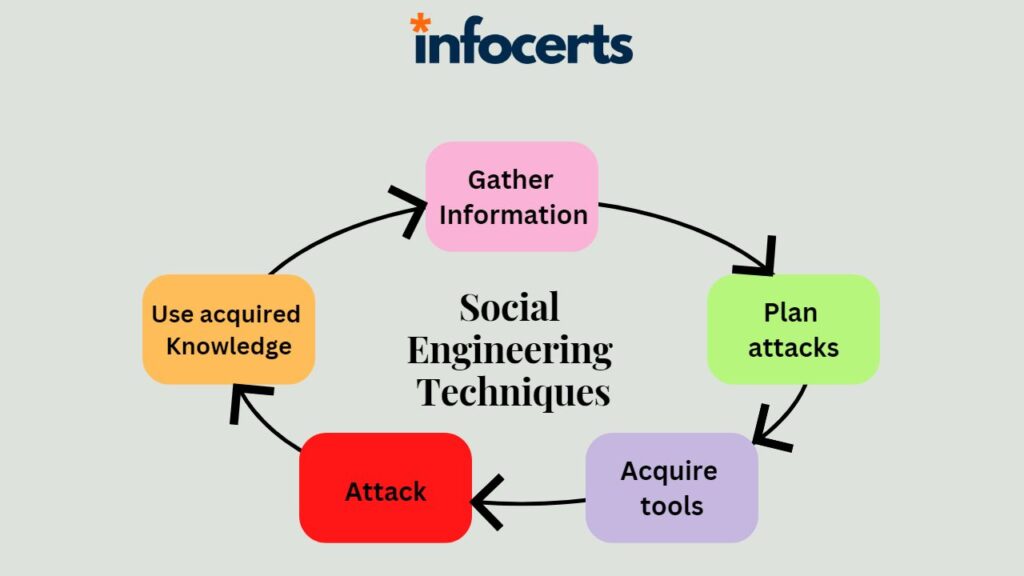
Social engineering techniques are becoming increasingly sophisticated, and as a Certified Ethical Hacker (CEH), it is essential to be aware of these techniques to prevent social engineering attacks. Social engineering involves using psychological manipulation to trick people into divulging sensitive information or performing an action that benefits the attacker. Social engineering is a serious threat to cybersecurity. Preventing social engineering attacks
Phishing is a common social engineering technique where attackers use fraudulent emails, messages, or websites to trick individuals into providing sensitive information such as usernames and passwords. Pretexting is another technique where attackers create a false scenario to gain access to sensitive information, such as impersonating a customer service representative to ask for personal information.
Baiting is another technique used by attackers where they offer something of value in exchange for personal information. For example, they may leave a USB drive with malicious software on it in a public place, hoping someone will pick it up and insert it into their computer. Finally, spear-phishing is a targeted attack where attackers gather information about specific individuals or organizations to create a customized attack.
To prevent social engineering attacks, it is important to implement best practices such as employee training, strong passwords, and multifactor authentication. Employee training can help individuals identify and report suspicious activity, while strong passwords and multifactor authentication can prevent attackers from gaining access to sensitive information.
| Type of Social Engineering Attack | Description | Example |
| Phishing | The use of emails or instant messages to trick individuals into clicking on links or downloading malicious attachments | An email claiming to be from a bank, asking the recipient to click on a link to update their account information |
| Pretexting | Creating a fake scenario or pretext to obtain sensitive information from unsuspecting individuals | A phone call claiming to be from IT support, asking for the user’s login credentials |
| Baiting | The use of tempting offers to entice individuals into clicking on links or opening malicious files | Leaving a USB drive labeled “Confidential” in a public area, hoping someone will plug it into their computer out of curiosity |
| Spear-phishing | A targeted attack that involves customized messages designed to appear trustworthy and obtain sensitive information | An email that appears to be from a CEO or other high-ranking official, requesting the recipient to transfer funds to a new account |
CEHs play a critical role in preventing social engineering attacks by conducting vulnerability assessments and identifying weaknesses in an organization’s security system. They can also conduct social engineering tests to assess an organization’s Awareness and preparedness for such attacks.
In conclusion, Social engineering is a serious threat to cybersecurity, and CEHs must be aware of these techniques to prevent them. By implementing best practices and staying informed, we can protect our sensitive information and safeguard against social engineering attacks.
Conclusion: Social engineering is a serious threat to cybersecurity, and it is crucial that individuals and organizations understand the common techniques used in these attacks. CEHs play a vital role in preventing social engineering attacks and Protecting Sensitive Information. By implementing best practices such as employee training, strong passwords, and multifactor authentication, we can significantly reduce the risk of social engineering attacks.
FAQs
Q1. What is social engineering?
Q2. What are some common types of social engineering attacks?
Q3. How can organizations prevent social engineering attacks?
Q4. What is the role of CEHs in combating social engineering attacks?
Q5. What techniques do CEHs use to identify and mitigate social engineering attacks?
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com