September 16, 2022
Android holds its position as the leading mobile phone operating system in worldwide. Having an Android phone is very common nowadays. Forensic testing of an Android phone is very crucial for every digital forensics experts.
In today’s digital forensics article we are going to learn about Andriller. Andriller is software utility with a collection of forensic tools for smartphones. It performs read-only, forensically sound, non-destructive acquisition from Android devices.
We learn how to install andriller on our Kali Linux system and use it against our own device.
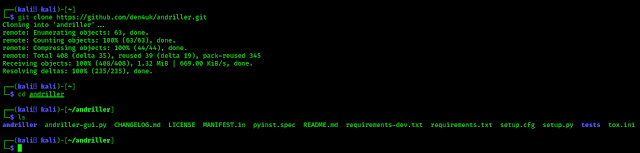
First of all we need to clone the GitHub repository of andriller on our system by applying following command;
After the cloning process complete we can navigate to the directory by using cd command:
Here we got some files but to install and use andriller we need to focus on two files they are setup.py and andriller-gui.py.
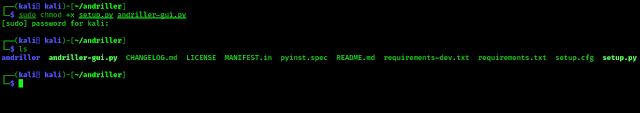
We set the permissions of both files using following command.
The following screeshot shows the output of applied command.
Now we can run the setup & install andriller. To do that we run following command on our terminal:
The above command will install all the dependencies to run this tool.
Here we recommended to run following command to install adb and python-tk for error-less works.
After installing the dependencies we can run the tool by simply using following command:
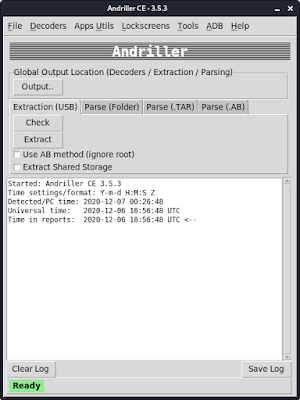
Then the GUI (Graphical User Interface) window of andriller will open in front of us as we can see in the following screenshot:
Here we need to set our “Output Location” we click there and set our output location. Here we choose our Desktop location.
Now we just need to connect an Android device with our Kali Linux system through USB, we need to use data cable here (USB debugging is must on Android device). After connecting data cable with the device we can use the “Check” option to check if our android device is connected or not.
After connecting our Android device we just need to click on “Extract” to get the report. After clicking on export we can see that our Android device is asking for backing up data here we just need to click on “back up my data”, as we did in the following screenshot:
Then our process will be started. If we have chosen or tick ✅ the “Shared Storage”, then Andriller will backup the whole storage which will be time consuming otherwise it will backup the system files only.
After completing the process the reports will be saved on our given location as a html file and browser opens the report automatically. As we can see in the following screenshot.
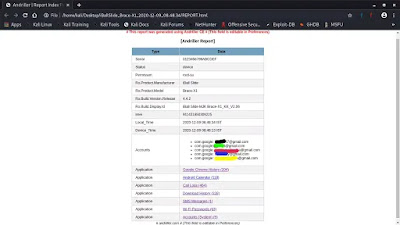 |
| Hided some personal information |
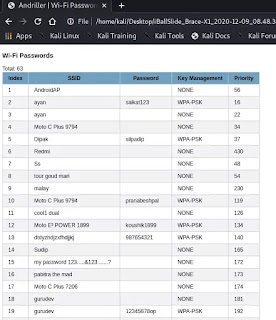
Here we can see the all details of the Android device. We can check the Google Accounts, Call logs, Browser history, WiFi passwords, SMS and much more.
Here is a screenshot of WiFi passwords.
Lots of information we can extract from an Android device using Andriller.
This is how we can perform digital forensics on an Android device. One more things, if we have a device with root permission then we can see the maximum results.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Article posted by: https://www.kalilinux.in/2020/12/andriller-forensic-of-android-on-kali-linux.html
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com
This is the article generated by feed coming from KaliLinux.in and Infocerts is only displaying the content.