Information security management — Guidelines for cyberinsurance
8 Role of ISMS in support of cyber-insurance
8.1 Overview
ISO/IEC 27001 provides organizations with a structured management framework for an ISMS designed to establish, implement, maintain and continually information security. An effective ISMS allows an organization to:
a) identify, analyze, and address its information security risks;
b) continually secure itself adequately against information security risks; and
c) review and improve information security controls to keep pace with changes to security threats, vulnerabilities and business impacts.
An ISMS can provide the insured and insurer with data, information and documentation that can be used in cyber-insurance policy inception, cyber-insurance policy renewal and throughout the lifetime of that cyber-insurance policy. Since cyber-insurance is a risk sharing option, providing cyber-risk management information to an insurer can assist the insurer to broker a more suitable cyber-insurance policy.
8.2 ISMS as a source of information
8.2.1 ISMS
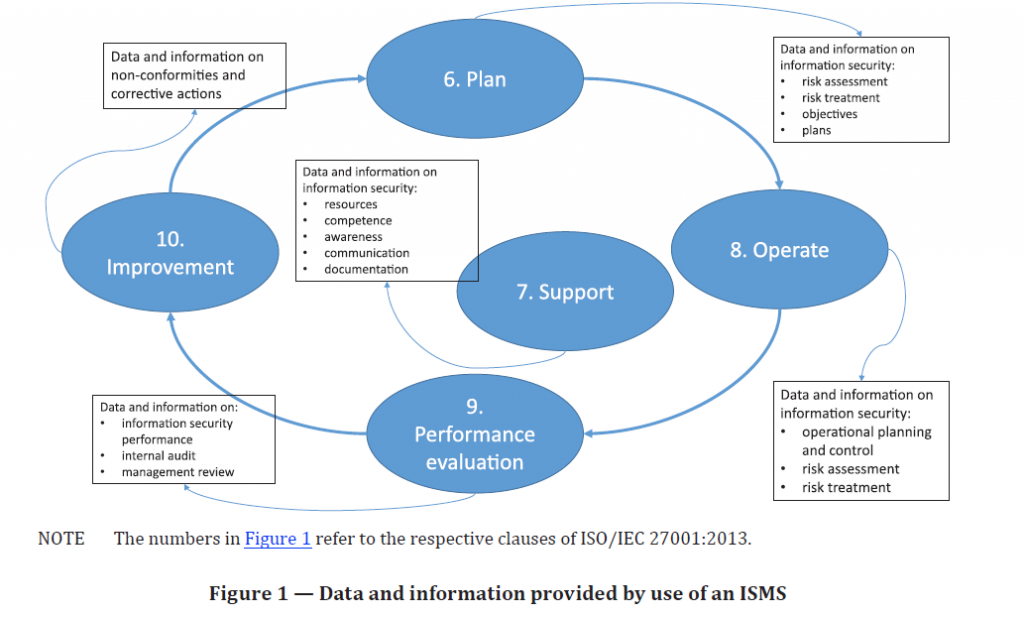
An ISMS that is established, implemented, maintained and continually improved in accordance with ISO/IEC 27001 can be used to collect data and information relevant to a cyber-insurance policy. Figure 1, based on ISO/IEC 27001:2013, provides examples of the information that can be produced from an ISMS.
The insured should collect and collate the outputs from its ISMS, information security measurement programmes (e.g. based on ISO/IEC 27004), and risk management activities (e.g. based on ISO/IEC 27005) and submit required data to an insurer. Annex A provides examples on the documentation that can be produced from the use of an ISMS by the insured.
8.2.2 Planning
In the planning, the insured determines the risks that need to be addressed to:
a)ensure the ISMS can achieve its intended outcome(s);
b)prevent, or reduce, undesired effects; and
c)achieve continual improvement.
The insured defines and applies an information security risk assessment and treatment process and retains relevant documented information.
Risk treatment plans determine the controls that the insured considers necessary to reduce cyber-risk. Such necessary controls are documented in the insured’s Statement of Applicability (SoA).
The documented information on the processes, risks identified and the risk assessment and treatment plans can be shared with an insurer.
8.2.3 Support
Individuals doing work under the insured’s control and leading or involved in establishing, implementing, maintaining and continually improving an ISMS need to be aware of:
a) the information security policy;
b) their contribution to the effectiveness of the ISMS, including the benefits of improved information security performance; and
c) the implications of not conforming with the ISMS requirements.
Information about awareness training of individuals can be shared with an insurer.
The insured determines the need for internal and external communications relevant to the ISMS including:
a) what to communicate on;
b) when to communicate;
c) whom to communicate with;
d) who communicates; and
e) the processes which cause communications to start.
The insured should apply the above guidance to determine how best to communicate with an insurer.
When implementing, operating or maintaining an ISMS, the insured creates the documentation:
a) as stated in ISO/IEC 27001; and
b) determined by the insured as being necessary for the effectiveness of the ISMS.
NOTE See ISO/IEC 27003 for examples of such additional documentation.
The documentation created above can be shared with an insurer.
8.2.4 Operation
When following the requirements of the ISMS during operations, the insured needs to:
a) plan, implement and control the processes needed to meet information security requirements, and implement the initial plans and actions determined in the planning phase;
b) keep documented information to the extent necessary to have confidence that defined processes have been carried out as planned;
c) control planned changes and review the consequences of unintended changes, taking action to mitigate any adverse effects, as necessary;
d) ensure that outsourced processes are determined and controlled;
e) perform information security risk assessments at planned intervals or when significant changes are proposed or occur, taking account of the criteria established in the planning phase, and retain documented information of the results of the information security risk assessments; and
f) implement the information security risk treatment plan and retain documented information of the results of the information security risk treatment.
The insured can share the documentation produced in this phase with an insurer.
8.2.5 Performance evaluation
Performance evaluations can produce data on the performance of information security controls (whether technical or otherwise), allowing the insured to collate and present information on the effectiveness and performance of those implemented controls. The data can be collected:
a) from the controls themselves;
b) by measurements of the controls;
c) by the use of metrics, such as those presented in ISO/IEC 27004;
d) by regular monitoring, review or assessment of the controls or the processes they support.
Internal audits of the information security function, information security controls or the ISMS can be used to gather further data on the efficiency and effectiveness of information security controls and the ISMS; and provide business context for this data. When required, third-party audits can also be used to gather this data.
Management reviews at planned intervals are required by the insured’s ISMS to ensure its continuing suitability, adequacy and effectiveness.
The data gathered from the evaluation phase can be used to identify non-conformance and areas requiring continual improvement and can also be captured as documented information which can be used as evidence of the monitoring and measurement results, which can be passed to an insurer.
The evaluation of information security can highlight new information security risks or changes in previously identified information security risks, which can be documented and shared with an insurer.
8.2.6 Improvement
When reacting to identified non-conformance, the steps taken assist in the treatment of information security risks. The treatment should be documented.
The insured can also document the steps taken to improve the suitability, adequacy and effectiveness of the ISMS. The insured can share the documentation on improvements of the ISMS with an insurer.
8.3 Sharing of information about risks and controls
As cyber-insurance is a risk sharing option that is part of the insured’s information security management, there is value in the insured regularly providing relevant cybersecurity information to an insurer. Such information exchange should be agreed between the insured and an insurer.
To create a cyber-insurance policy, both the insured and an insurer exchange information so that:
a) the insured can demonstrate its efforts to protect itself from cyber-threats;
b) the insured can define which risks it wants to share; and
c) an insurer estimates the risk it is accepting and then creates and prices a cyber-insurance policy, including applicable deductibles or exclusions.
The information should be as complete and as up-to-date as possible. Failure to do so can invalidate or revoke the cyber-insurance policy, so that the insured cannot make a claim. Providing false information can invalidate the cyber-insurance policy and can lead to legal action against the insured or individuals involved in providing that false information.
The insured should have a process to respond to an insurer’s requests for data and information at cyber-insurance policy inception, cyber-insurance policy renewal, at defined intervals during the lifetime of the cyber-insurance policy and if a cyber-incident occurs. The insured should also produce the data and information required by an insurer in an agreed format. The insured should be able to present to an insurer, on request, any documentation held by the insured relating to its information security or cyber-risk activities. Such documents can include ISMS documentation, internal or external audit reports and follow-up results, information security or security certifications held by the insured or individuals, as well as policies, procedures, and guidelines.
8.4 Meeting cyber-insurance policy obligations
An insurer can require a level of security as a precondition of coverage. Such conditions are usually stated in the cyber-insurance policy, and the insured needs to meet these conditions during the validity of the contract.
Further, when applying for cyber-insurance coverage, the insured can be asked to share information about the adopted information security controls. These controls should be maintained during the validity of the contract.
An ISMS can assist the insured in completing cyber-insurance policy questionnaires and making sure the insured meets the obligations as set out in a cyber-insurance policy.
People also ask this Questions
- What are the aspects of coverage?
- What data are covered by cyber liability insurance?
- Are there any regional restrictions on the policy?
- How long after a breach occurs do you have to report it without losing coverage?
- What is cyber insurance?
- What is cyber risk?
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com


