August 28, 2021
TIDos Web Application Penetration Testing Framework
Tidos Framework is an open source toolkit that performs all major web application tests, such as: B. Enlightenment, scanning, enumeration, and vulnerability analysis.
All tasks are performed in phases with the integrated modules. The total number of modules exceeds 100, most of which are used for recognition and vulnerability assessments.
Here is what the Tidos framework consists of:
A comprehensive and versatile framework that covers everything from education to vulnerability analysis.
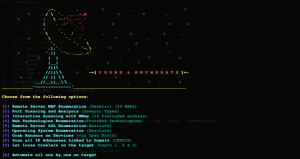
Has 5 main phases, divided into 14 sub-phases with a total of 108 modules.
The illumination phase has 50 clean modules (including active and passive education, information disclosure modules).
The analysis and enumeration phase consists of 16 modules (including port analysis, WAF analysis, etc.).
The Vulnerability Analysis Phase consists of 37 modules (including the most common vulnerabilities in action).
Exploits Castle has only one feat. (purely development policy)
And finally, Auxillaries has 4 modules. more in development
The four phases each have an auto-awesome module that automates each module for you.
You just need the domain and leave everything to this tool.
TIDoS provides comprehensive support so you know what’s going on.
Friendly interaction environment. (no shit)
How to install and run TIDoS-Framework :
git clone https://github.com/0xinfection/tidos-framework.git
cd tidos-framework![]()
- Install the dependencies:
chmod +x install
./install
Immaculate properties:
TIDoS Framework currently supports the following: Other modules are under development.
Clarification + OSINT
Passive lights:
Nping Enumeration via an external APi
Collect information on the whois search domain
GeoIP Search Locate the physical location
DNSDump DNS Configuration Search
Search for indexed subdomains
reverse DNS lookup hosts
Reverse IP Search Hosts on the Same Server
Subnet enumeration class
IP Instances of Domain IP History
Indexed Web Gatherer
Manual search in Google
Google Dorking (multiple modules) automated
Send an e-mail to the domain resolver
Wayback Machine Search Search Backups
Out of E-mail Verification of Pwned Email Accounts
Listed only through Google Groups emails
Check the availability of aliases on social networks
Find PasteBin Domain-Based Messages
LinkedIn bringing together employees and companies
Google Plus is collecting domain profiles
Public contact Scraping CONTACT COMPLETE
Censys Intel Gathering Domain Based
Threat Intelligence Collects Invalid IP Addresses
Active Education:
Advanced ping enumeration
CMS detection (185+ CMS supported) ENHANCED
Advanced traceroute IMPROVED
Robots.txt checker and sitemap.xml
Live capture of HTTP headers
Use OPTIONS to search for allowed HTTP methods.
Determine the server type ENHANCED
Check the absolute SSL certificate
Apache Status Disclosure Verification File Based
Enumeration WebDAV HTTP PROFIND & SEARCH
Enumeration of PHPInfo files via Bruteforce
Comments Scraper Regex Based
Search for shared DNS hosts based on a name server
Discovery of alternative sites based on the user agent
Discover interesting files with Bruteforce
Shells frequently used for backdoor locations, etc.
Common backup locations .bak, .db, and so on.
Common storage locations for .pgp, .skr, and other passwords.
Common proxy path configuration. .pac etc.
Multiple index index paths, index1 etc.
Common point files .htaccess, .apache, etc.
Common locations for .log, .changelog, and other log files.
Disclosure of information:
Disclosure of Credit Cards in Clear Text
E-mail Harvester IMPROVED
The fatal enumeration error contains the full path
Internal intellectual property communication based on signature
Telephone number based on the Havester signature
Number of social security of American collectors
Digitization and enumeration
Generic WAF enumeration for remote server 54 WAF
Ingenious modules for port scanning
Simple port scanner on socket connections
TCP SYN Scan Very reliable
Very reliable scan of TCP connections
XMAS indicator scan Reliable only in local area networks
FIN Flag Scan Reliable only in local area networks
Port Service Detector
Enumeration of Absolute Web Technology
Absolute absolute SSL enumeration
Fingerprint operating system IMPROVED
Banners capture services through open ports
Interactive scanning with NMap preinstalled modules 16
Analysis of Internet servers with the CENSYS database
Crawlers for websites and links
Depth 1 Indexed Uri Crawler
Depth 2 single page Crawler
Depth 3 Web Link Crawler
Vulnerability Analysis
Web bugs and server configuration errors
CORS Absolute dangerous
Based on a script subdomain on the same site
DNS zone transfer based on the server
jacking
Busting controls framework
X-FRAME-OPTIONS Header Checks
Security with cookies
HttpOnly flag
Safe flag on cookies
Cloudflare test for misconfiguration
checks DNS for misconfiguration
Search the online database for violations
Use strict HTTP transport security
HTTPS enabled, but no HSTS
Usurpation of email by domain
Missing SPF records
Missing DMARC records
host header injection
Port based on the web socket
X-Forwarded-For header injection
Live Capture security header analysis
Trace between locations of the HTTP TRACE method
Session correction by cookie injection
Network security is not configured correctly.
Check if TELNET is enabled via port 23
Serious security breaches on the Web
file inclusions
LFI (Local File Inclusion) -Param
Enhanced Remote File Inclusion (RFI)
parameters based on
Based on the pre-installed path
OS Command Injection for Linux and Windows (RCE)
Trails crossing (sensitive paths)
Inter-site query absolute falsification
SQL injection
Injection based on errors
Value based cookie
Reference value
Value of the user agent based
Automatic gathering
Other Tools:
net_info.py– Displays information about your network. Located undertools/.tidos_updater.py– Updates the framework to the latest release via signature matching. Located undertools/.
TIDoS In Action:
The TIDoS Framework
Web Application Penetration Testing Course
Ddos2Track – HTTP Floods attacks
Article posted by: https://hackingresources.com/tidos-web-application-penetration-testing-framework/
——————————————————————————————————————–
Infocerts, 5B 306 Riverside Greens, Panvel, Raigad 410206 Maharashtra, India
Contact us – https://www.infocerts.com