CEH VS PENTEST
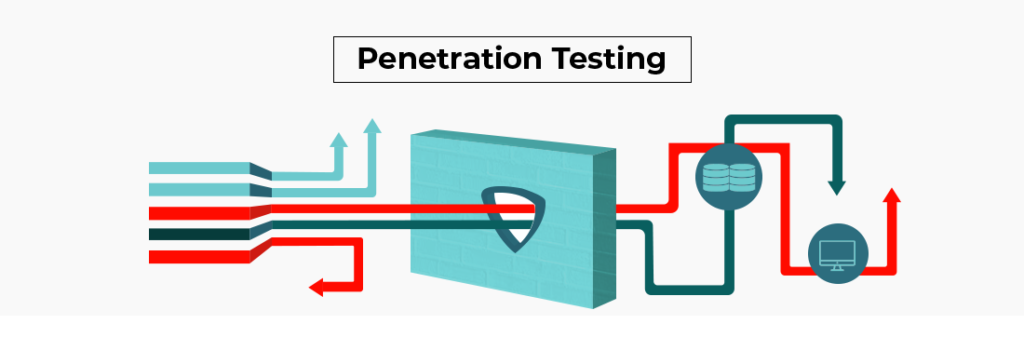
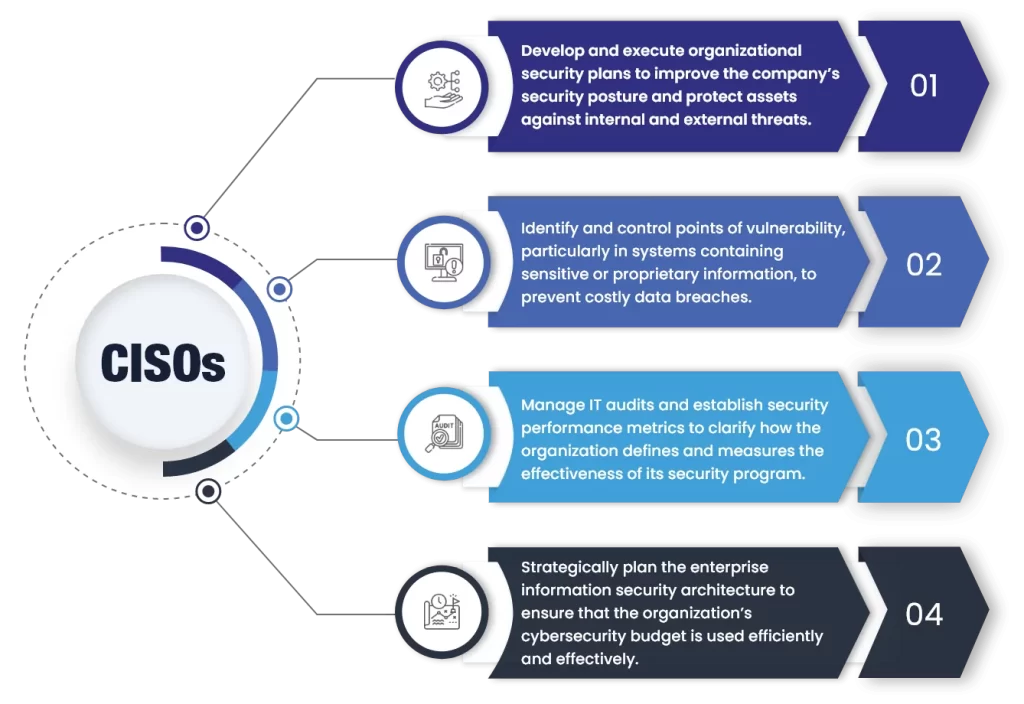
As this article shows, the comparison of CEH to Pentest+ is misleading. In a nutshell, you would not compare a cake to flour, as it makes no sense to compare an entire dish to a single ingredient. Ethical hacking on its own is NOT pen-testing. Penetration testing focuses on the security of the specific area…
The post CEH VS PENTEST appeared first on Cybersecurity Exchange.