How to Become An Enterprise Architect
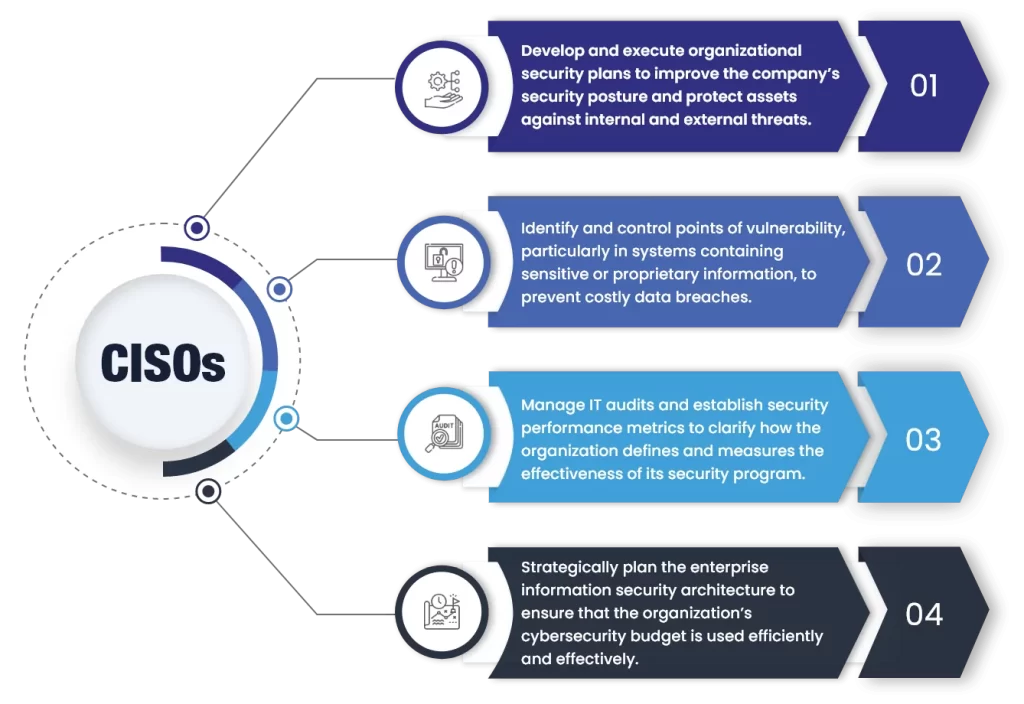
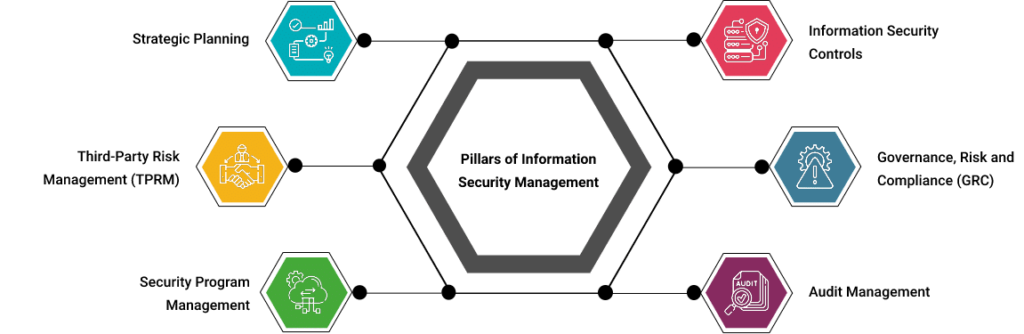
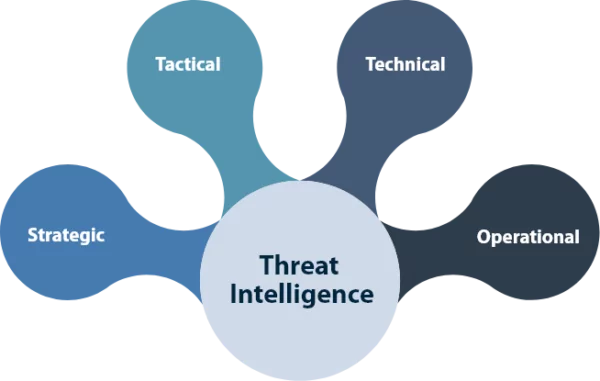
An Enterprise Architect develops and maintains business, systems, and information processes to support enterprise security architecture; develops information technology (IT) rules and requirements that describe baseline and target architectures. Enterprise architecture (EA) is a discipline for proactively and holistically leading enterprise responses to disruptive forces by identifying and analyzing the execution of change towards desired…
The post How to Become An Enterprise Architect appeared first on Cybersecurity Exchange.