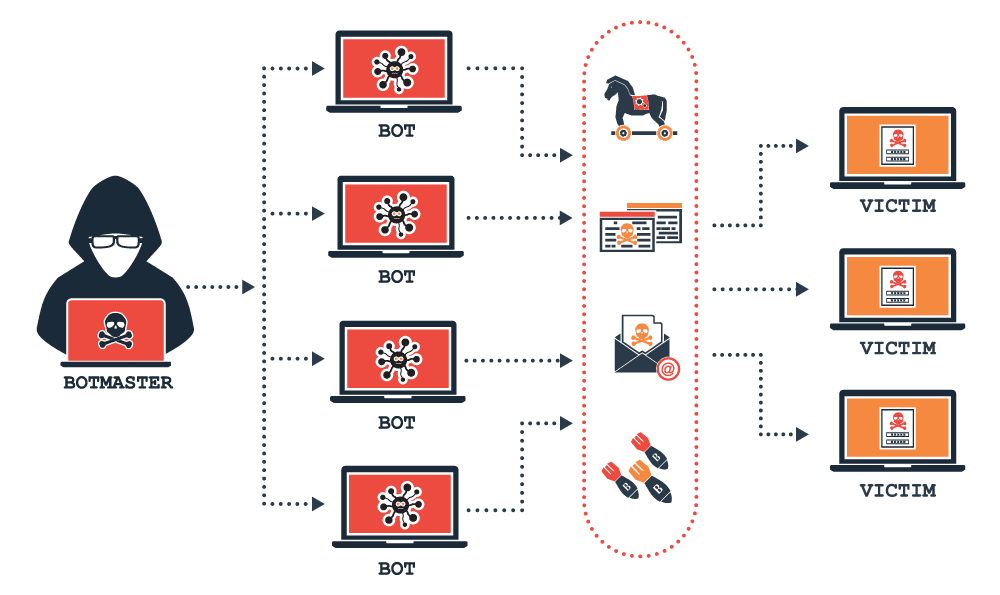
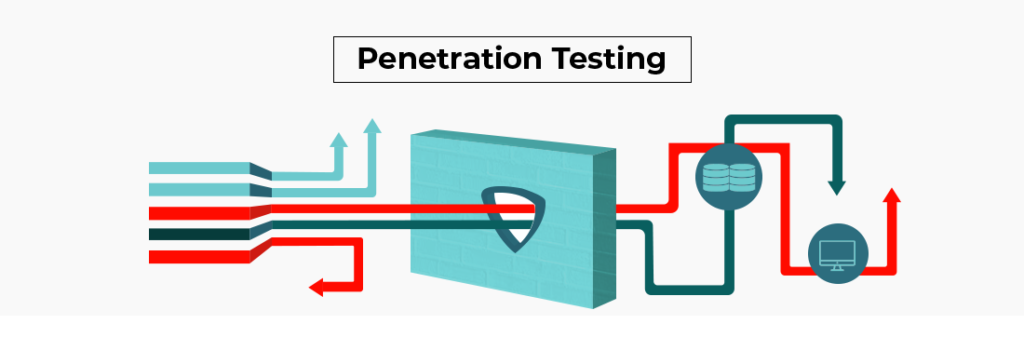
Navigating the Cybersecurity Landscape: Unlocking Basics for Beginners
Date: April 16, 2024 Time: 2:30 PM BST | 9:30 AM EDT | 7:00 PM IST Topic: Navigating the Cybersecurity Landscape: Unlocking Basics for Beginners Register Abstract: In today’s digital landscape, cybersecurity has become paramount. With the rise in the quality and quantity of cyber threats, the traditional approach for the active and passive defense…
The post Navigating the Cybersecurity Landscape: Unlocking Basics for Beginners appeared first on Cybersecurity Exchange.